According to Greek mythology, the Greeks won the Trojan War by entering in to the fortified city of Troy hiding in a huge, hollow wooden horse. The Greeks built a huge wooden horse for their soldiers to hide in. They left the horse in front of the gates of Troy. The Trojans thought it to be a gift from the Greeks, who had withdrawn from the war, and so they transported the horse into their city. At night, the Spartan soldiers broke through the wooden horse, and opened the gates for their soldiers who eventually destroyed the city of Troy.
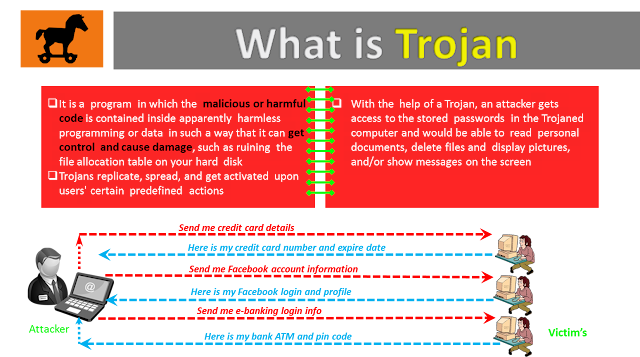
Taking a cue from Greek mythology, a computer Trojan is defined as a "malicious, security breaking program that is disguised as something benign." A computer Trojan horse is used to enter a victim's computer undetected, granting the attacker unrestricted access to the data stored on that computer and causing immense damage to the victim. For example, a user downloads what appears to be a movie or a music file, but when he or she runs it, it unleashes a dangerous program that may erase the unsuspecting user's disk and send his or her credit card numbers and passwords to a stranger. A Trojan can also be wrapped into a legitimate program, meaning that this program may have hidden functionality that the user is unaware of.
In another scenario, a victim may also be used as an intermediary to attack others—without his or her knowledge. Attackers can use the victim's computer to commit illegal denial-of-service attacks such as those that virtually crippled the DALnet IRC network for months on end.
(DALnet is an Internet relay chat (IRC) network that is a form of instant communication over the network.) Trojan horses work on the same level of privileges that the victim user has. If the victim had the privileges, Trojan can delete files, transmit information, modify existing files, and install other programs (such as programs that provide unauthorized network access and execute privilege elevation attacks). The Trojan horse can attempt to exploit a vulnerability to increase the level of access beyond that of the user running the Trojan horse. If successful, the Trojan horse can operate with increased privileges and may install other malicious codes on the victim's machine.
A compromise of any system on a network may affect the other systems on the network. Systems that transmit authentication credentials such as passwords over shared networks in clear text or in a trivially encrypted form are particularly vulnerable. If a system on such a network is compromised, the intruder may be able to record user names and passwords or other sensitive information.
Additionally, a Trojan, depending on the actions it performs, may falsely implicate the remote system as the source of an attack by spoofing and, thereby, cause the remote system to incur liabilities.
ReplyDeleteافضل شركة عزل اسطح براس التنورة
افضل شركة مكافحة النمل الابيض بالاحساء
افضل شركة تسليك مجاري بالخبر
افضل شركة كشف تسربات المياة بالدمام
افضل شركة كشف تسربات المياة بالاحساء
Invest in Ripple on eToro the World’s Best Social Trading Network!
ReplyDeleteJoin millions who have already discovered easier methods for investing in Ripple...
Learn from established eToro traders or copy their trades automatically!
Your blog was absolutely fantastic! Great deal of great information and this can be useful some or maybe the other way.
ReplyDeleteForeign Currency Exchange San Francisco